The cybersecurity market is expected to grow from USD 175.2 billion in 2020 to USD 362.11 billion by 2028, at a CAGR of 9.5% during the forecast period 2021-2028.
Cybersecurity is the application of defending servers, computers, mobile devices, data, software, electronic system, and networks from malicious attacks, unauthorized access, and damage. Enterprises and individuals use cybersecurity to protect the system against unauthorized access to computerized systems and data centers. A powerful cybersecurity strategy provides a robust security posture against malicious attacks constructed to alter, access, delete, extort or destroy a user's or organization's sensitive data and system. Cybersecurity is instrumental in averting attacks that aim to disrupt and disable a device's or system's operation. Cyber-attack can severely cost an organization as they expose the data to hackers with ulterior motives.
The rise in adoption of Internet of Things (IoT) solutions in cloud security and industrial control systems has triggered the need & need for cybersecurity. Similarly, the increase in advanced technologies such as big data, artificial intelligence, and 5G across several industries has fuelled the demand for cybersecurity. The surge in cyber-attacks in retail, BFSI, IT & telecom, healthcare, manufacturing, energy, and defense & government leads to data exposure. Hence, to minimize & avoid cyber-attack, many organizations are adopting cybersecurity which has caused a spike in demand for cybersecurity. These are the factors driving the global cybersecurity market. Factors such as lack of in-house expertise, IT resources, and knowledge of IAM solutions are creating challenges in the growth of the global cybersecurity market.
This study delivers a comprehensive analysis of security type, component, end-use, and region. The security type segment includes cloud application security, network security, internet security, and end-point security. Cloud application security is leading the security type segment. The growth is attributed to acceleration in the acceptance of cloud technology across enterprises due to data breach risk related to cloud solutions. The rising risk of unauthorized access, malware infiltrations, and a hike in the number of cyber threats across cloud layers has compelled organizations to adopt cloud security services and solutions. The component segment involves software, product, and service. The software is leading the component segment. The growth is attributed to the rise in demand for software solutions such as SCADA encryption, DDoS firewall, antivirus, malware, virtualization security, backup & recovery, etc. The leading players aim to develop advanced industrial security software for industries such as oil & gas, energy, automotive, etc. The end-use segment involves retail, BFSI, IT & telecom, healthcare, manufacturing, energy, and defense & government. The healthcare segment is leading the end-use segment. The growth is attributed to the rise in cybercrimes and cyber-attacks in the healthcare industry over the years. The cybercrimes in the healthcare industry involve data breaches, insider threats, advanced malware attacks, distributed denial of service, and ransomware compromising the system's patient care security and integrity.
The market has been divided into North America, Europe, Asia-Pacific, Middle East & Africa, and South America. North America is leading the regional segment. The growth is attributed to eminent security providers with regional and global headquarters in the U.S. Therefore, the rise in spending on security services and solutions by SMEs and large enterprises in North America has driven the cybersecurity market. The Asia-Pacific ranks second as cybersecurity solution faces demand from the energy, finance, telecom, and technology sectors to eliminate cyber threats and risks.
Some notable players in the cybersecurity market are IBM Corporation, Schneider Electric, ABB Ltd., Mcafee LLC, Cisco Systems Inc., Microsoft Corporation, Honeywell International Inc., Siemens AG, Splunk Inc., Trend Micro Inc., Dell Inc., etc.
Cyber Security Market Analysis and Forecast, Security Type
Cyber Security Market Analysis and Forecast, Component
Cyber Security Market Analysis and Forecast, End-use
Cyber Security Market Analysis and Forecast, Region
Report Description:
1. Introduction
1.1. Objectives of the Study
1.2. Market Definition
1.3. Research Scope
1.4. Currency
1.5. Key Target Audience
2. Research Methodology and Assumptions
3. Executive Summary
4. Premium Insights
4.1. Porter’s Five Forces Analysis
4.2. Value Chain Analysis
4.3. Top Investment Pockets
4.3.1. Market Attractiveness Analysis By Component
4.3.2. Market Attractiveness Analysis By End-use
4.3.3. Market Attractiveness Analysis By Security Type
4.3.4. Market Attractiveness Analysis By Region
4.4. Industry Trends
5. Market Dynamics
5.1. Market Evaluation
5.2. Drivers
5.2.1. Protection against unauthorized access
5.2.2. Rise in use of cyber security in healthcare
5.2.3. Surge in cyber-attacks
5.3. Restrains
5.3.1. Lack of IT resources
5.3.2. Lack of in-house expertise
5.4. Opportunities
5.4.1. Demand from Asia-Pacific region developing countries
6. Global Cyber Security Market Analysis and Forecast, By Component
6.1. Segment Overview
6.2. Software
6.3. Service
6.4. Product
7. Global Cyber Security Market Analysis and Forecast, By End-use
7.1. Segment Overview
7.2. IT & Telecom
7.3. BSFI
7.4. Manufacturing
7.5. Retail
7.6. Healthcare
7.7. Defence & Government
7.8. Energy
8. Global Cyber Security Market Analysis and Forecast, By Security Type
8.1. Segment Overview
8.2. Cloud application security
8.3. Network security
8.4. Internet security
8.5. End-point security
9. Global Cyber Security Market Analysis and Forecast, By Regional Analysis
9.1. Segment Overview
9.2. North America
9.2.1. U.S.
9.2.2. Canada
9.2.3. Mexico
9.3. Europe
9.3.1. Germany
9.3.2. France
9.3.3. U.K.
9.3.4. Italy
9.3.5. Spain
9.4. Asia-Pacific
9.4.1. Japan
9.4.2. China
9.4.3. India
9.5. South America
9.5.1. Brazil
9.6. Middle East and Africa
9.6.1. UAE
9.6.2. South Africa
10. Global Cyber Security Market-Competitive Landscape
10.1. Overview
10.2. Market Share of Key Players in Global Cyber Security Market
10.2.1. Global Company Market Share
10.2.2. North America Company Market Share
10.2.3. Europe Company Market Share
10.2.4. APAC Company Market Share
10.3. Competitive Situations and Trends
10.3.1. Component Launches and Developments
10.3.2. Partnerships, Collaborations, and Agreements
10.3.3. Mergers & Acquisitions
10.3.4. Expansions
11. Company Profiles
11.1. IMB Corporation
11.1.1. Business Overview
11.1.2. Company Snapshot
11.1.3. Company Market Share Analysis
11.1.4. Company Product Portfolio
11.1.5. Recent Developments
11.1.6. SWOT Analysis
11.2. Microsoft Corporation
11.2.1. Business Overview
11.2.2. Company Snapshot
11.2.3. Company Market Share Analysis
11.2.4. Company Product Portfolio
11.2.5. Recent Developments
11.2.6. SWOT Analysis
11.3. Schneider Electric
11.3.1. Business Overview
11.3.2. Company Snapshot
11.3.3. Company Market Share Analysis
11.3.4. Company Product Portfolio
11.3.5. Recent Developments
11.3.6. SWOT Analysis
11.4. Honeywell International Inc.
11.4.1. Business Overview
11.4.2. Company Snapshot
11.4.3. Company Market Share Analysis
11.4.4. Company Product Portfolio
11.4.5. Recent Developments
11.4.6. SWOT Analysis
11.5. ABB lts
11.5.1. Business Overview
11.5.2. Company Snapshot
11.5.3. Company Market Share Analysis
11.5.4. Company Product Portfolio
11.5.5. Recent Developments
11.5.6. SWOT Analysis
11.6. Mcafee LLC
11.6.1. Business Overview
11.6.2. Company Snapshot
11.6.3. Company Market Share Analysis
11.6.4. Company Product Portfolio
11.6.5. Recent Developments
11.6.6. SWOT Analysis
11.7. Cisco System Inc
11.7.1. Business Overview
11.7.2. Company Snapshot
11.7.3. Company Market Share Analysis
11.7.4. Company Product Portfolio
11.7.5. Recent Developments
11.7.6. SWOT Analysis
11.8. Dell Inc.
11.8.1. Business Overview
11.8.2. Company Snapshot
11.8.3. Company Market Share Analysis
11.8.4. Company Product Portfolio
11.8.5. Recent Developments
11.8.6. SWOT Analysis
11.9. Siemens AG
11.9.1. Business Overview
11.9.2. Company Snapshot
11.9.3. Company Market Share Analysis
11.9.4. Company Product Portfolio
11.9.5. Recent Developments
11.9.6. SWOT Analysis
11.10. Splunk Inc.
11.10.1. Business Overview
11.10.2. Company Snapshot
11.10.3. Company Market Share Analysis
11.10.4. Company Product Portfolio
11.10.5. Recent Developments
11.10.6. SWOT Analysis
11.11. Trend Micro Inc.
11.11.1. Business Overview
11.11.2. Company Snapshot
11.11.3. Company Market Share Analysis
11.11.4. Company Product Portfolio
11.11.5. Recent Developments
11.11.6. SWOT Analysis
List of Table
1. Global Cyber Security Market, By End-use, 2018-2028 (USD Billion)
2. Global IT & Telecom, Cyber Security Market, By Region, 2018-2028 (USD Billion)
3. Global Retail, Cyber Security Market, By Region, 2018-2028 (USD Billion)
4. Global Healthcare, Cyber Security Market, By Region, 2018-2028 (USD Billion)
5. Global Defence & Government, Cyber Security Market, By Region, 2018-2028 (USD Billion)
6. Global Energy, Cyber Security Market, By Region, 2018-2028 (USD Billion)
7. Global Manufacturing, Cyber Security Market, By Region, 2018-2028 (USD Billion)
8. Global Cyber Security Market, By Component, 2018-2028 (USD Billion)
9. Global Software, Cyber Security Market, By Region, 2018-2028 (USD Billion)
10. Global Service, Cyber Security Market, By Region, 2018-2028 (USD Billion)
11. Global Product, Cyber Security Market, By Region, 2018-2028 (USD Billion)
12. Global Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
13. Global Cloud Application Security, Cyber Security Market, By Region, 2018-2028 (USD Billion)
14. Global Network Security, Cyber Security Market, By Region, 2018-2028 (USD Billion)
15. Global Internet Security, Cyber Security Market, By Region, 2018-2028 (USD Billion)
16. Global End-point Security, Cyber Security Market, By Region, 2018-2028 (USD Billion)
17. North America Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
18. North America Cyber Security Market, By Component, 2018-2028 (USD Billion)
19. North America Cyber Security Market, By End-use, 2018-2028 (USD Billion)
20. U.S. Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
21. U.S. Cyber Security Market, By Component, 2018-2028 (USD Billion)
22. U.S. Cyber Security Market, By End-use, 2018-2028 (USD Billion)
23. Canada Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
24. Canada Cyber Security Market, By Component, 2018-2028 (USD Billion)
25. Canada Cyber Security Market, By End-use, 2018-2028 (USD Billion)
26. Mexico Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
27. Mexico Cyber Security Market, By Component, 2018-2028 (USD Billion)
28. Mexico Cyber Security Market, By End-use, 2018-2028 (USD Billion)
29. Europe Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
30. Europe Cyber Security Market, By Component, 2018-2028 (USD Billion)
31. Europe Cyber Security Market, By End-use, 2018-2028 (USD Billion)
32. Germany Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
33. Germany Cyber Security Market, By Component, 2018-2028 (USD Billion)
34. Germany Cyber Security Market, By End-use, 2018-2028 (USD Billion)
35. France Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
36. France Cyber Security Market, By Component, 2018-2028 (USD Billion)
37. France Cyber Security Market, By End-use, 2018-2028 (USD Billion)
38. U.K. Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
39. U.K. Cyber Security Market, By Component, 2018-2028 (USD Billion)
40. U.K. Cyber Security Market, By End-use, 2018-2028 (USD Billion)
41. Italy Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
42. Italy Cyber Security Market, By Component, 2018-2028 (USD Billion)
43. Italy Cyber Security Market, By End-use, 2018-2028 (USD Billion)
44. Spain Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
45. Spain Cyber Security Market, By Component, 2018-2028 (USD Billion)
46. Spain Cyber Security Market, By End-use, 2018-2028 (USD Billion)
47. Asia Pacific Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
48. Asia Pacific Cyber Security Market, By Component, 2018-2028 (USD Billion)
49. Asia Pacific Cyber Security Market, By End-use, 2018-2028 (USD Billion)
50. Japan Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
51. Japan Cyber Security Market, By Component, 2018-2028 (USD Billion)
52. Japan Cyber Security Market, By End-use, 2018-2028 (USD Billion)
53. China Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
54. China Cyber Security Market, By Component, 2018-2028 (USD Billion)
55. China Cyber Security Market, By End-use, 2018-2028 (USD Billion)
56. India Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
57. India Cyber Security Market, By Component, 2018-2028 (USD Billion)
58. India Cyber Security Market, By End-use, 2018-2028 (USD Billion)
59. South America Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
60. South America Cyber Security Market, By Component, 2018-2028 (USD Billion)
61. South America Cyber Security Market, By End-use, 2018-2028 (USD Billion)
62. Brazil Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
63. Brazil Cyber Security Market, By Component, 2018-2028 (USD Billion)
64. Brazil Cyber Security Market, By End-use, 2018-2028 (USD Billion)
65. Middle East and Africa Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
66. Middle East and Africa Cyber Security Market, By Component, 2018-2028 (USD Billion)
67. Middle East Cyber Security Market, By End-use, 2018-2028 (USD Billion)
68. UAE Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
69. UAE Cyber Security Market, By Component, 2018-2028 (USD Billion)
70. UAE Cyber Security Market, By End-use, 2018-2028 (USD Billion)
71. South Africa Cyber Security Market, By Security Type, 2018-2028 (USD Billion)
72. South Africa Cyber Security Market, By Component, 2018-2028 (USD Billion)
73. South Africa Cyber Security Market, By End-use, 2018-2028 (USD Billion)
List of Figures
1. Global Cyber Security Market Segmentation
2. Global Cyber Security Market: Research Methodology
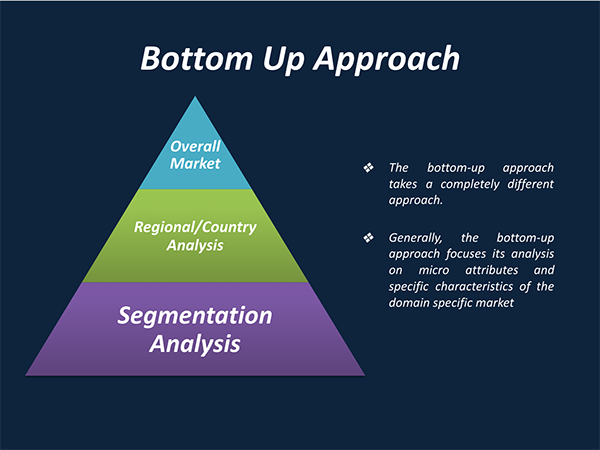
3. Market Size Estimation Methodology: Bottom-Up Approach
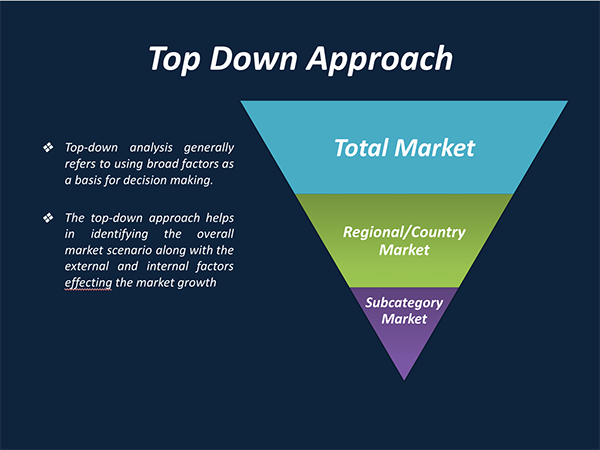
4. Market Size Estimation Methodology: Top-Down Approach
5. Data Triangulation
6. Porter’s Five Forces Analysis
7. Value Chain Analysis
8. Global Cyber Security Market Attractiveness Analysis By Security Type
9. Global Cyber Security Market Attractiveness Analysis By Component
10. Global Cyber Security Market Attractiveness Analysis By End-use
11. Global Cyber Security Market Attractiveness Analysis By Region
12. Global Cyber Security Market: Dynamics
13. Global Cyber Security Market Share by Security Type (2021 & 2028)
14. Global Cyber Security Market Share by Component (2021 & 2028)
15. Global Cyber Security Market Share by End-use (2021 & 2028)
16. Global Cyber Security Market Share by Regions (2021 & 2028)
17. Global Cyber Security Market Share by Company (2020)
Market research is a method of gathering, assessing and deducing data & information about a particular market. Market research is very crucial in these days. The techniques analyze about how a product/service can be offered to the market to its end-customers, observe the impact of that product/service based on the past customer experiences, and cater their needs and demands. Owing to the successful business ventures, accurate, relevant and thorough information is the base for all the organizations because market research report/study offers specific market related data & information about the industry growth prospects, perspective of the existing customers, and the overall market scenario prevailed in past, ongoing present and developing future. It allows the stakeholders and investors to determine the probability of a business before committing substantial resources to the venture. Market research helps in solving the marketing issues challenges that a business will most likely face.
Market research is valuable because of the following reasons:
Our research report features both the aspects; qualitative and quantitative. Qualitative part provides insights about the market driving forces, potential opportunities, customer’s demands and requirement which in turn help the companies to come up with new strategies in order to survive in the long run competition. The quantitative segment offers the most credible information related to the industry. Based on the data gathering, we use to derive the market size and estimate their future growth prospects on the basis of global, region and country.
Our market research process involves with the four specific stages.
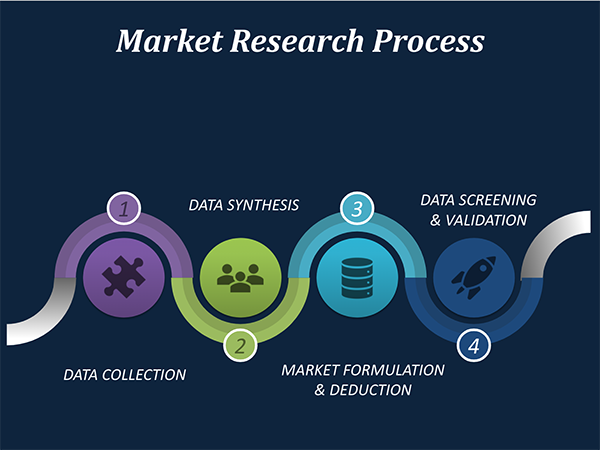
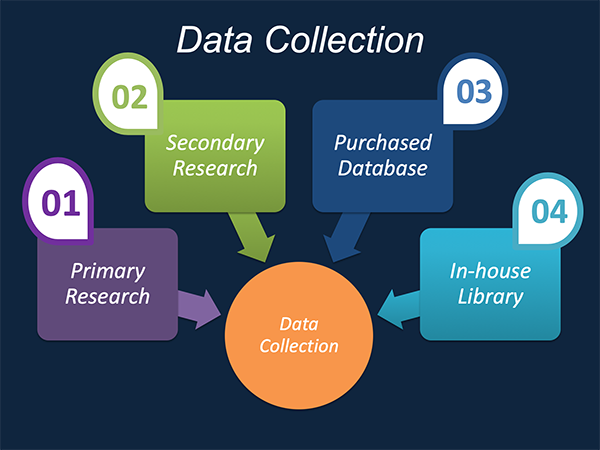
Data Collection: This stage of the market research process involves with the gathering and collecting of the market/industry related data from the sources. There are basically two types of research methods:
Data Synthesis: This stage includes the evaluation and assessment of all the data acquired from the primary and secondary research. It likewise includes in evaluating the information for any disparity watched while information gathering identified with the market. The data & information is gathered with consideration to the heterogeneity of sources. Scientific and statistical methods are implemented for synthesizing dissimilar information sets and provide the relevant data which is fundamental for formulating strategies. Our organization has broad involvement with information amalgamation where the information goes through different stages:
Market Formulation & Deduction: The last stage includes assigning the data & information in a suitable way in order to derive market size. Analyst reviews and domain based opinions based on holistic approach of market estimation combined with industry investigation additionally features a crucial role in this stage.
This stage includes with the finalization of the market size and numbers that we have gathered from primary and secondary research. With the data & information addition, we ensure that there is no gap in the market information. Market trend analysis is finished by our analysts by utilizing data extrapolation procedures, which give the most ideal figures to the market.
Data Validation: Validation is the most crucial step in the process. Validation & re-validation through scientifically designed technique and process that helps us finalize data-points to be used for final calculations. This stage also involves with the data triangulation process. Data triangulation generally implicates the cross validation and matching the data which has been collected from primary and secondary research methods.













































Free Customization
Countries can be added on demand
Free yearly update on purchase of Multi/Corporate User License
Companies served till date

We serve our customers 24x7 for 365 days through calls, emails and live chat options.

Huge database of exceptional market reports bringing market intelligence to your fingertips.

SSL enabled, we offer you various secured payment options for risk free purchase.