The Endpoint Security Market is expected to grow from USD 13.53 billion in 2020 to USD 24.61 billion by 2028, at a CAGR of 7.77% during the forecast period 2021-2028.
Endpoint security is the discipline of preventing malicious campaigns from exploiting endpoints or entry points of end-user devices such as PCs, laptops, and mobile devices. Cybersecurity risks are protected by endpoint security solutions on a network or in the cloud. Endpoint security has progressed beyond antivirus software to complete protection against sophisticated malware and emerging zero-day threats. Nation-states, hacktivists, organized crime, and deliberate and unintentional insider threats pose a hazard to businesses of all sizes. Endpoint security is sometimes referred to as the frontline of cybersecurity, and it is one of the first locations that enterprises try to safeguard their networks. The demand for increasingly powerful endpoint security solutions has increased in tandem with the number and sophistication of cybersecurity attacks. Today's endpoint security solutions are built to rapidly identify, analyse, stop, and contain ongoing threats. To do so, they must work together and with other security technologies to provide administrators with visibility into advanced threats, allowing them to respond more quickly to detection and remediation.
The factors driving the endpoint security market are, Hackers may readily access corporate data with sophisticated cellphones. As a result, securing the enterprise's confidential data necessitates protecting and tracing every internal operation. The rising usage of remote location servers, smartphones, and connected gadgets has increased the number of endpoints in businesses. Attacks and data breaches may become more likely as endpoints become more numerous. Endpoint solutions maintain track of harmful activities and device behavior while securing every endpoint. As a result, the endpoint security industry is expected to increase as BYOD policies become more widely implemented. The factors restraining the outdoor furniture market growth are that Many businesses are suffering from a scarcity of qualified technical personnel to manage their security systems. Providing continual training to technical employees is extremely expensive, especially for SMEs, as technology evolves. Employers find it challenging to hire dedicated cybersecurity specialists, according to the 2018 McAfee Cyber Security Talent Report. According to a Gartner report, fast-changing digital solutions are also contributing to the growing skills shortages. As a result, endpoint protection solutions uptake is likely to be hampered. Organizations must, however, perform periodic digital skills training to overcome such hurdles.
Artificial intelligence is being looked at as a possible option for preventing external attacks and data breaches. Endpoint protection has become increasingly important as the number of end-user devices, interfaces, and sophisticated technologies like cloud services, 5G, and the internet of things has grown.
This study delivers a comprehensive analysis of enforcement point and development. The Enforcement Point segment includes server, workstation, mobile devices, point of sale terminal. The mobile devices enforcement point segment dominated the endpoint security segment market in 2020. The quantity of application and essential data stored on mobile endpoints is enormous. Mobile endpoints have been recognized as a primary target for cyber attackers. The development segment includes cloud, on-premise. The cloud development segment dominated the endpoint security segment market in 2020 as Additional costs can be saved by using customized services.
The endpoint security market has been divided into North America, Europe, Asia-Pacific, Middle East & Africa, and South America. The Asia-Pacific dominated the endpoint security market with 36.49% in 2020, followed by North America. The Asia-Pacific area is predicted to see substantial expansion. The significant presence of SMEs in the region, who use a range of endpoint security apps, drives the sector's rapid growth. Due to substantial investment in IT infrastructure, widespread internet use, and increasing use of intelligent devices, the area has the fastest-growing endpoint security industry. Because of the fast digital transition and its vulnerability to cyberattacks, all of these factors function as drivers for the endpoint security industry. In the worldwide endpoint security industry, North America is the fastest revenue generator. The endpoint security sector in the area is undergoing substantial transformations. The increased adoption of this technology in North America may be ascribed to the expanding usage of automation and behavioral analysis for threat detection, the growing volume of data across sectors, and rising company spending in real-time security solutions.
Some of the notable players in the endpoint security market are Symantec, Kaspersky, Carbon Black, TrendMicro, Sophos, Microsoft, CrowdStrike, McAfee, SentinelOne, and ESET.
Global Endpoint Security Market Analysis and Forecast, by Enforcement Point
Global Endpoint Security Market Analysis and Forecast, by Development
Global Endpoint Security Market Analysis and Forecast, by Region
Report Description:
1. Introduction
1.1. Objectives of the Study
1.2. Market Definition
1.3. Research Scope
1.4. Currency
1.5. Key Target Audience
2. Research Methodology and Assumptions
3. Executive Summary
4. Premium Insights
4.1. Porter’s Five Forces Analysis
4.2. Value Chain Analysis
4.3. Top Investment Pockets
4.3.1. Market Attractiveness Analysis by Enforcement Point
4.3.2. Market Attractiveness Analysis by Development
4.3.3. Market Attractiveness Analysis By region
4.4. Industry Trends
5. Market Dynamics
5.1. Market Evaluation
5.2. Drivers
5.2.1. Increasing Endpoint Attacks and Breaches
5.3. Restrains
5.3.1. Use of Free or Pirated Endpoint Protection Solutions
5.4. Opportunities
5.4.1. Rapid Rise in Demand for Integrated Endpoint Security Infrastructure and Software
6. Global Endpoint Security Market Analysis and Forecast, By Enforcement Point
6.1. Segment Overview
6.2. Server
6.3. Workstation
6.4. Mobile Devices
6.5. Point of Sale Terminal
7. Global Endpoint Security Market Analysis and Forecast, By Development
7.1. Segment Overview
7.2. Cloud
7.3. On-premise
8. Global Endpoint Security Market Analysis and Forecast, By Regional Analysis
8.1. Segment Overview
8.2. North America
8.2.1. U.S.
8.2.2. Canada
8.2.3. Mexico
8.3. Europe
8.3.1. Germany
8.3.2. France
8.3.3. U.K.
8.3.4. Italy
8.3.5. Spain
8.4. Asia-Pacific
8.4.1. Japan
8.4.2. China
8.4.3. India
8.5. South America
8.5.1. Brazil
8.6. Middle East and Africa
8.6.1. UAE
8.6.2. South Africa
9. Global Endpoint Security Market-Competitive Landscape
9.1. Overview
9.2. Market Share of Key Players in Global Endpoint Security Market
9.2.1. Global Company Market Share
9.2.2. North America Company Market Share
9.2.3. Europe Company Market Share
9.2.4. APAC Company Market Share
9.3. Competitive Situations and Trends
9.3.1. Product Launches and Developments
9.3.2. Partnerships, Collaborations, and Agreements
9.3.3. Mergers & Acquisitions
9.3.4. Expansions
10. Company Profiles
10.1. Symantec
10.1.1. Business Overview
10.1.2. Company Snapshot
10.1.3. Company Market Share Analysis
10.1.4. Company Product Portfolio
10.1.5. Recent Developments
10.1.6. SWOT Analysis
10.2. Kaspersky
10.2.1. Business Overview
10.2.2. Company Snapshot
10.2.3. Company Market Share Analysis
10.2.4. Company Product Portfolio
10.2.5. Recent Developments
10.2.6. SWOT Analysis
10.3. Carbon Black
10.3.1. Business Overview
10.3.2. Company Snapshot
10.3.3. Company Market Share Analysis
10.3.4. Company Product Portfolio
10.3.5. Recent Developments
10.3.6. SWOT Analysis
10.4. TrendMicro
10.4.1. Business Overview
10.4.2. Company Snapshot
10.4.3. Company Market Share Analysis
10.4.4. Company Product Portfolio
10.4.5. Recent Developments
10.4.6. SWOT Analysis
10.5. Sophos
10.5.1. Business Overview
10.5.2. Company Snapshot
10.5.3. Company Market Share Analysis
10.5.4. Company Product Portfolio
10.5.5. Recent Developments
10.5.6. SWOT Analysis
10.6. Microsoft
10.6.1. Business Overview
10.6.2. Company Snapshot
10.6.3. Company Market Share Analysis
10.6.4. Company Product Portfolio
10.6.5. Recent Developments
10.6.6. SWOT Analysis
10.7. CrowdStrike
10.7.1. Business Overview
10.7.2. Company Snapshot
10.7.3. Company Market Share Analysis
10.7.4. Company Product Portfolio
10.7.5. Recent Developments
10.7.6. SWOT Analysis
10.8. McAfee
10.8.1. Business Overview
10.8.2. Company Snapshot
10.8.3. Company Market Share Analysis
10.8.4. Company Product Portfolio
10.8.5. Recent Developments
10.8.6. SWOT Analysis
10.9. SentinelOne
10.9.1. Business Overview
10.9.2. Company Snapshot
10.9.3. Company Market Share Analysis
10.9.4. Company Product Portfolio
10.9.5. Recent Developments
10.9.6. SWOT Analysis
10.10. ESET
10.10.1. Business Overview
10.10.2. Company Snapshot
10.10.3. Company Market Share Analysis
10.10.4. Company Product Portfolio
10.10.5. Recent Developments
10.10.6. SWOT Analysis
List of Table
1. Global Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
2. Global Server, Endpoint Security Market, By Region, 2018-2028 (USD Billion)
3. Global Workstation, Endpoint Security Market, By Region, 2018-2028 (USD Billion)
4. Global Mobile Devices, Endpoint Security Market, By Region, 2018-2028 (USD Billion)
5. Global Point of Sale Terminal, Endpoint Security Market, By Region, 2018-2028 (USD Billion)
6. Global Endpoint Security Market, By Development, 2018-2028 (USD Billion)
7. Global Cloud, Endpoint Security Market, By Region, 2018-2028 (USD Billion)
8. Global On-premise, Endpoint Security Market, By Region, 2018-2028 (USD Billion)
9. North America Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
10. North America Endpoint Security Market, By Development, 2018-2028 (USD Billion)
11. U.S. Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
12. U.S. Endpoint Security Market, By Development, 2018-2028 (USD Billion)
13. Canada Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
14. Canada Endpoint Security Market, By Development, 2018-2028 (USD Billion)
15. Mexico Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
16. Mexico Endpoint Security Market, By Development, 2018-2028 (USD Billion)
17. Europe Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
18. Europe Endpoint Security Market, By Development, 2018-2028 (USD Billion)
19. Germany Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
20. Germany Endpoint Security Market, By Development, 2018-2028 (USD Billion)
21. France Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
22. France Endpoint Security Market, By Development, 2018-2028 (USD Billion)
23. U.K. Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
24. U.K. Endpoint Security Market, By Development, 2018-2028 (USD Billion)
25. Italy Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
26. Italy Endpoint Security Market, By Development, 2018-2028 (USD Billion)
27. Spain Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
28. Spain Endpoint Security Market, By Development, 2018-2028 (USD Billion)
29. Asia Pacific Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
30. Asia Pacific Endpoint Security Market, By Development, 2018-2028 (USD Billion)
31. Japan Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
32. Japan Endpoint Security Market, By Development, 2018-2028 (USD Billion)
33. China Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
34. China Endpoint Security Market, By Development, 2018-2028 (USD Billion)
35. India Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
36. India Endpoint Security Market, By Development, 2018-2028 (USD Billion)
37. South America Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
38. South America Endpoint Security Market, By Development, 2018-2028 (USD Billion)
39. Brazil Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
40. Brazil Endpoint Security Market, By Development, 2018-2028 (USD Billion)
41. Middle East and Africa Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
42. Middle East and Africa Endpoint Security Market, By Development, 2018-2028 (USD Billion)
43. UAE Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
44. UAE Endpoint Security Market, By Development, 2018-2028 (USD Billion)
45. South Africa Endpoint Security Market, By Enforcement Point, 2018-2028 (USD Billion)
46. South Africa Endpoint Security Market, By Development, 2018-2028 (USD Billion)
List of Figures
1. Global Endpoint Security Market Segmentation
2. Global Endpoint Security Market: Research Methodology
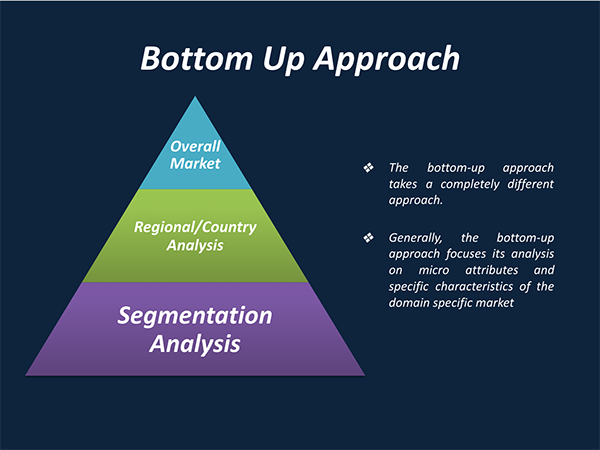
3. Market Size Estimation Methodology: Bottom-Up Approach
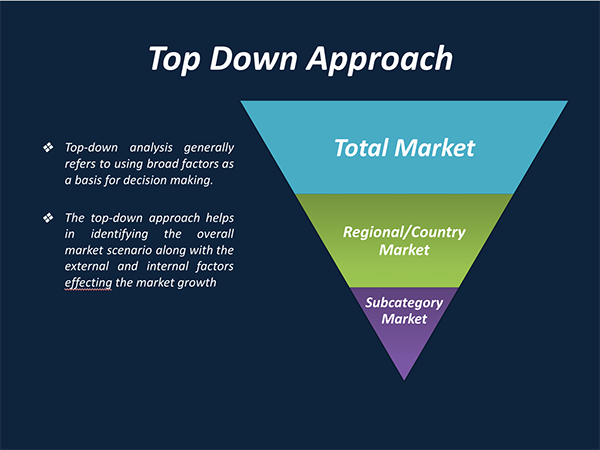
4. Market Size Estimation Methodology: Top-Down Approach
5. Data Triangulation
6. Porter’s Five Forces Analysis
7. Value Chain Analysis
8. Global Endpoint Security Market Attractiveness Analysis by Enforcement Point
9. Global Endpoint Security Market Attractiveness Analysis by Development
10. Global Endpoint Security Market Attractiveness Analysis by Region
11. Global Endpoint Security Market: Dynamics
12. Global Endpoint Security Market Share by Enforcement Point (2021 - 2028)
13. Global Endpoint Security Market Share by Development (2021 - 2028)
14. Global Endpoint Security Market Share by Regions (2021 - 2028)
15. Global Endpoint Security Market Share by Company (2020)
Market research is a method of gathering, assessing and deducing data & information about a particular market. Market research is very crucial in these days. The techniques analyze about how a product/service can be offered to the market to its end-customers, observe the impact of that product/service based on the past customer experiences, and cater their needs and demands. Owing to the successful business ventures, accurate, relevant and thorough information is the base for all the organizations because market research report/study offers specific market related data & information about the industry growth prospects, perspective of the existing customers, and the overall market scenario prevailed in past, ongoing present and developing future. It allows the stakeholders and investors to determine the probability of a business before committing substantial resources to the venture. Market research helps in solving the marketing issues challenges that a business will most likely face.
Market research is valuable because of the following reasons:
Our research report features both the aspects; qualitative and quantitative. Qualitative part provides insights about the market driving forces, potential opportunities, customer’s demands and requirement which in turn help the companies to come up with new strategies in order to survive in the long run competition. The quantitative segment offers the most credible information related to the industry. Based on the data gathering, we use to derive the market size and estimate their future growth prospects on the basis of global, region and country.
Our market research process involves with the four specific stages.
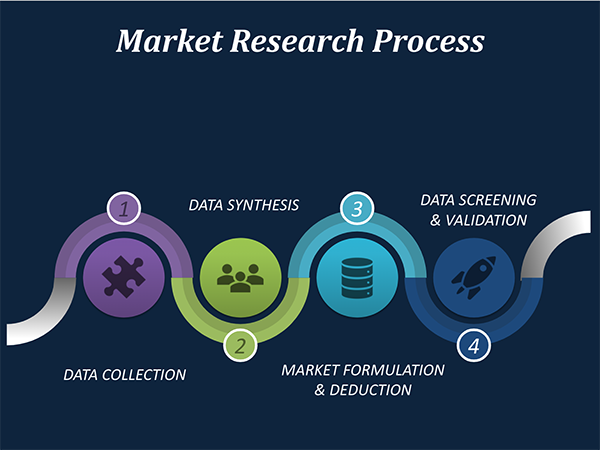
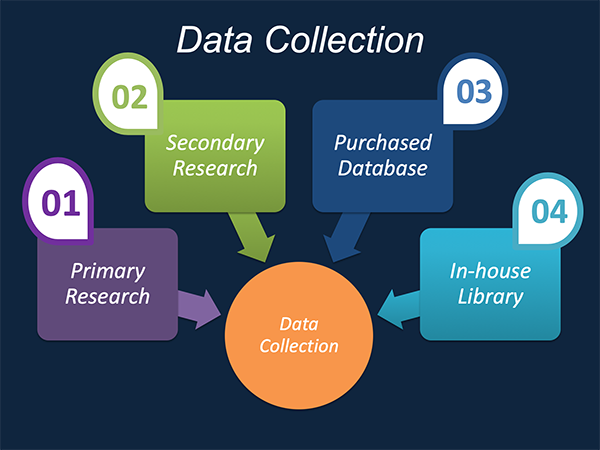
Data Collection: This stage of the market research process involves with the gathering and collecting of the market/industry related data from the sources. There are basically two types of research methods:
Data Synthesis: This stage includes the evaluation and assessment of all the data acquired from the primary and secondary research. It likewise includes in evaluating the information for any disparity watched while information gathering identified with the market. The data & information is gathered with consideration to the heterogeneity of sources. Scientific and statistical methods are implemented for synthesizing dissimilar information sets and provide the relevant data which is fundamental for formulating strategies. Our organization has broad involvement with information amalgamation where the information goes through different stages:
Market Formulation & Deduction: The last stage includes assigning the data & information in a suitable way in order to derive market size. Analyst reviews and domain based opinions based on holistic approach of market estimation combined with industry investigation additionally features a crucial role in this stage.
This stage includes with the finalization of the market size and numbers that we have gathered from primary and secondary research. With the data & information addition, we ensure that there is no gap in the market information. Market trend analysis is finished by our analysts by utilizing data extrapolation procedures, which give the most ideal figures to the market.
Data Validation: Validation is the most crucial step in the process. Validation & re-validation through scientifically designed technique and process that helps us finalize data-points to be used for final calculations. This stage also involves with the data triangulation process. Data triangulation generally implicates the cross validation and matching the data which has been collected from primary and secondary research methods.













































Free Customization
Countries can be added on demand
Free yearly update on purchase of Multi/Corporate User License
Companies served till date

We serve our customers 24x7 for 365 days through calls, emails and live chat options.

Huge database of exceptional market reports bringing market intelligence to your fingertips.

SSL enabled, we offer you various secured payment options for risk free purchase.