Market Overview
The global Phishing Protection market size is expected to gain market growth in the forecast period of 2020 to 2025, with a CAGR of xx% in the forecast period of 2020 to 2025 and will expected to reach USD xx million by 2025, from USD xx million in 2019.
The Phishing Protection market report provides a detailed analysis of global market size, regional and country-level market size, segmentation market growth, market share, competitive Landscape, sales analysis, impact of domestic and global market players, value chain optimization, trade regulations, recent developments, opportunities analysis, strategic market growth analysis, product launches, area marketplace expanding, and technological innovations.
Market segmentation
Phishing Protection market is split by Type and by Application. For the period 2015-2025, the growth among segments provide accurate calculations and forecasts for sales by Type and by Application in terms of volume and value. This analysis can help you expand your business by targeting qualified niche markets.
By Type, Phishing Protection market has been segmented into:
Email based Phishing
Non-email based Phishing
By Application, Phishing Protection has been segmented into:
BFSI
Government
Healthcare
Telecommunication and IT
Transportation
Education
Retail
Regions and Countries Level Analysis
Regional analysis is another highly comprehensive part of the research and analysis study of the global Phishing Protection market presented in the report. This section sheds light on the sales growth of different regional and country-level Phishing Protection markets. For the historical and forecast period 2015 to 2025, it provides detailed and accurate country-wise volume analysis and region-wise market size analysis of the global Phishing Protection market.
The report offers in-depth assessment of the growth and other aspects of the Phishing Protection market in important countries (regions), including:
North America (United States, Canada and Mexico)
Europe (Germany, France, UK, Russia and Italy)
Asia-Pacific (China, Japan, Korea, India, Southeast Asia and Australia)
South America (Brazil, Argentina, Colombia)
Middle East and Africa (Saudi Arabia, UAE, Egypt, Nigeria and South Africa)
Competitive Landscape and Phishing Protection Market Share Analysis
Phishing Protection competitive landscape provides details by vendors, including company overview, company total revenue (financials), market potential, global presence, Phishing Protection sales and revenue generated, market share, price, production sites and facilities, SWOT analysis, product launch. For the period 2015-2020, this study provides the Phishing Protection sales, revenue and market share for each player covered in this report.
The major players covered in Phishing Protection are:
Cyren
Cisco Systems Inc.
FireEye Inc.
BAE Systems
GreatHorn, Inc.
Microsoft Corporation
Intel Corporation
Proofpoint, Inc.
Symantec Corporation
Phishlabs
Mimecast Ltd.
Table of Contents
1 Phishing Protection Market Overview
1.1 Product Overview and Scope of Phishing Protection
1.2 Classification of Phishing Protection by Type
1.2.1 Global Phishing Protection Revenue by Type: 2015 VS 2019 VS 2025
1.2.2 Global Phishing Protection Revenue Market Share by Type in 2019
1.2.3 Email based Phishing
1.2.4 Non-email based Phishing
1.3 Global Phishing Protection Market by Application
1.3.1 Overview: Global Phishing Protection Revenue by Application: 2015 VS 2019 VS 2025
1.3.2 BFSI
1.3.3 Government
1.3.4 Healthcare
1.3.5 Telecommunication and IT
1.3.6 Transportation
1.3.7 Education
1.3.8 Retail
1.4 Global Phishing Protection Market by Regions
1.4.1 Global Phishing Protection Market Size by Regions: 2015 VS 2019 VS 2025
1.4.2 Global Market Size of Phishing Protection (2015-2025)
1.4.3 North America (USA, Canada and Mexico) Phishing Protection Status and Prospect (2015-2025)
1.4.4 Europe (Germany, France, UK, Russia and Italy) Phishing Protection Status and Prospect (2015-2025)
1.4.5 Asia-Pacific (China, Japan, Korea, India and Southeast Asia) Phishing Protection Status and Prospect (2015-2025)
1.4.6 South America (Brazil, Argentina, Colombia) Phishing Protection Status and Prospect (2015-2025)
1.4.7 Middle East & Africa (Saudi Arabia, UAE, Egypt, Nigeria and South Africa) Phishing Protection Status and Prospect (2015-2025)
2 Company Profiles
2.1 Cyren
2.1.1 Cyren Details
2.1.2 Cyren Major Business and Total Revenue (Financial Highlights) Analysis
2.1.3 Cyren SWOT Analysis
2.1.4 Cyren Product and Services
2.1.5 Cyren Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.2 Cisco Systems Inc.
2.2.1 Cisco Systems Inc. Details
2.2.2 Cisco Systems Inc. Major Business and Total Revenue (Financial Highlights) Analysis
2.2.3 Cisco Systems Inc. SWOT Analysis
2.2.4 Cisco Systems Inc. Product and Services
2.2.5 Cisco Systems Inc. Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.3 FireEye Inc.
2.3.1 FireEye Inc. Details
2.3.2 FireEye Inc. Major Business and Total Revenue (Financial Highlights) Analysis
2.3.3 FireEye Inc. SWOT Analysis
2.3.4 FireEye Inc. Product and Services
2.3.5 FireEye Inc. Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.4 BAE Systems
2.4.1 BAE Systems Details
2.4.2 BAE Systems Major Business and Total Revenue (Financial Highlights) Analysis
2.4.3 BAE Systems SWOT Analysis
2.4.4 BAE Systems Product and Services
2.4.5 BAE Systems Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.5 GreatHorn, Inc.
2.5.1 GreatHorn, Inc. Details
2.5.2 GreatHorn, Inc. Major Business and Total Revenue (Financial Highlights) Analysis
2.5.3 GreatHorn, Inc. SWOT Analysis
2.5.4 GreatHorn, Inc. Product and Services
2.5.5 GreatHorn, Inc. Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.6 Microsoft Corporation
2.6.1 Microsoft Corporation Details
2.6.2 Microsoft Corporation Major Business and Total Revenue (Financial Highlights) Analysis
2.6.3 Microsoft Corporation SWOT Analysis
2.6.4 Microsoft Corporation Product and Services
2.6.5 Microsoft Corporation Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.7 Intel Corporation
2.7.1 Intel Corporation Details
2.7.2 Intel Corporation Major Business and Total Revenue (Financial Highlights) Analysis
2.7.3 Intel Corporation SWOT Analysis
2.7.4 Intel Corporation Product and Services
2.7.5 Intel Corporation Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.8 Proofpoint, Inc.
2.8.1 Proofpoint, Inc. Details
2.8.2 Proofpoint, Inc. Major Business and Total Revenue (Financial Highlights) Analysis
2.8.3 Proofpoint, Inc. SWOT Analysis
2.8.4 Proofpoint, Inc. Product and Services
2.8.5 Proofpoint, Inc. Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.9 Symantec Corporation
2.9.1 Symantec Corporation Details
2.9.2 Symantec Corporation Major Business and Total Revenue (Financial Highlights) Analysis
2.9.3 Symantec Corporation SWOT Analysis
2.9.4 Symantec Corporation Product and Services
2.9.5 Symantec Corporation Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.10 Phishlabs
2.10.1 Phishlabs Details
2.10.2 Phishlabs Major Business and Total Revenue (Financial Highlights) Analysis
2.10.3 Phishlabs SWOT Analysis
2.10.4 Phishlabs Product and Services
2.10.5 Phishlabs Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
2.11 Mimecast Ltd.
2.11.1 Mimecast Ltd. Details
2.11.2 Mimecast Ltd. Major Business and Total Revenue (Financial Highlights) Analysis
2.11.3 Mimecast Ltd. SWOT Analysis
2.11.4 Mimecast Ltd. Product and Services
2.11.5 Mimecast Ltd. Phishing Protection Revenue, Gross Margin and Market Share (2018-2019)
3 Market Competition, by Players
3.1 Global Phishing Protection Revenue and Share by Players (2015-2020)
3.2 Market Concentration Rate
3.2.1 Top 5 Phishing Protection Players Market Share
3.2.2 Top 10 Phishing Protection Players Market Share
3.3 Market Competition Trend
4 Market Size by Regions
4.1 Global Phishing Protection Revenue and Market Share by Regions
4.2 North America Phishing Protection Revenue and Growth Rate (2015-2020)
4.3 Europe Phishing Protection Revenue and Growth Rate (2015-2020)
4.4 Asia-Pacific Phishing Protection Revenue and Growth Rate (2015-2020)
4.5 South America Phishing Protection Revenue and Growth Rate (2015-2020)
4.6 Middle East & Africa Phishing Protection Revenue and Growth Rate (2015-2020)
5 North America Phishing Protection Revenue by Countries
5.1 North America Phishing Protection Revenue by Countries (2015-2020)
5.2 USA Phishing Protection Revenue and Growth Rate (2015-2020)
5.3 Canada Phishing Protection Revenue and Growth Rate (2015-2020)
5.4 Mexico Phishing Protection Revenue and Growth Rate (2015-2020)
6 Europe Phishing Protection Revenue by Countries
6.1 Europe Phishing Protection Revenue by Countries (2015-2020)
6.2 Germany Phishing Protection Revenue and Growth Rate (2015-2020)
6.3 UK Phishing Protection Revenue and Growth Rate (2015-2020)
6.4 France Phishing Protection Revenue and Growth Rate (2015-2020)
6.5 Russia Phishing Protection Revenue and Growth Rate (2015-2020)
6.6 Italy Phishing Protection Revenue and Growth Rate (2015-2020)
7 Asia-Pacific Phishing Protection Revenue by Countries
7.1 Asia-Pacific Phishing Protection Revenue by Countries (2015-2020)
7.2 China Phishing Protection Revenue and Growth Rate (2015-2020)
7.3 Japan Phishing Protection Revenue and Growth Rate (2015-2020)
7.4 Korea Phishing Protection Revenue and Growth Rate (2015-2020)
7.5 India Phishing Protection Revenue and Growth Rate (2015-2020)
7.6 Southeast Asia Phishing Protection Revenue and Growth Rate (2015-2020)
8 South America Phishing Protection Revenue by Countries
8.1 South America Phishing Protection Revenue by Countries (2015-2020)
8.2 Brazil Phishing Protection Revenue and Growth Rate (2015-2020)
8.3 Argentina Phishing Protection Revenue and Growth Rate (2015-2020)
9 Middle East & Africa Revenue Phishing Protection by Countries
9.1 Middle East & Africa Phishing Protection Revenue by Countries (2015-2020)
9.2 Saudi Arabia Phishing Protection Revenue and Growth Rate (2015-2020)
9.3 UAE Phishing Protection Revenue and Growth Rate (2015-2020)
9.4 Egypt Phishing Protection Revenue and Growth Rate (2015-2020)
9.5 South Africa Phishing Protection Revenue and Growth Rate (2015-2020)
10 Market Size Segment by Type
10.1 Global Phishing Protection Revenue and Market Share by Type (2015-2020)
10.2 Global Phishing Protection Market Forecast by Type (2019-2024)
10.3 Email based Phishing Revenue Growth Rate (2015-2025)
10.4 Non-email based Phishing Revenue Growth Rate (2015-2025)
11 Global Phishing Protection Market Segment by Application
11.1 Global Phishing Protection Revenue Market Share by Application (2015-2020)
11.2 Phishing Protection Market Forecast by Application (2019-2024)
11.3 BFSI Revenue Growth (2015-2020)
11.4 Government Revenue Growth (2015-2020)
11.5 Healthcare Revenue Growth (2015-2020)
11.6 Telecommunication and IT Revenue Growth (2015-2020)
11.7 Transportation Revenue Growth (2015-2020)
11.8 Education Revenue Growth (2015-2020)
11.9 Retail Revenue Growth (2015-2020)
12 Global Phishing Protection Market Size Forecast (2021-2025)
12.1 Global Phishing Protection Market Size Forecast (2021-2025)
12.2 Global Phishing Protection Market Forecast by Regions (2021-2025)
12.3 North America Phishing Protection Revenue Market Forecast (2021-2025)
12.4 Europe Phishing Protection Revenue Market Forecast (2021-2025)
12.5 Asia-Pacific Phishing Protection Revenue Market Forecast (2021-2025)
12.6 South America Phishing Protection Revenue Market Forecast (2021-2025)
12.7 Middle East & Africa Phishing Protection Revenue Market Forecast (2021-2025)
13 Research Findings and Conclusion
14 Appendix
14.1 Methodology
14.2 Data Source
14.3 Disclaimer
14.4 About US
List of Tables
Table 1. Global Phishing Protection Revenue (USD Million) by Type: 2015 VS 2019 VS 2025
Table 2. Breakdown of Phishing Protection by Company Type (Tier 1, Tier 2 and Tier 3)
Table 3. Global Phishing Protection Revenue (USD Million) by Application: 2015 VS 2019 VS 2025
Table 4. Global Market Phishing Protection Revenue (Million USD) Comparison by Regions 2015-2025
Table 5. Cyren Corporate Information, Location and Competitors
Table 6. Cyren Phishing Protection Major Business
Table 7. Cyren Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 8. Cyren SWOT Analysis
Table 9. Cyren Phishing Protection Product and Solutions
Table 10. Cyren Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 11. Cisco Systems Inc. Corporate Information, Location and Competitors
Table 12. Cisco Systems Inc. Phishing Protection Major Business
Table 13. Cisco Systems Inc. Phishing Protection Total Revenue (USD Million) (2018-2019)
Table 14. Cisco Systems Inc. SWOT Analysis
Table 15. Cisco Systems Inc. Phishing Protection Product and Solutions
Table 16. Cisco Systems Inc. Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 17. FireEye Inc. Corporate Information, Location and Competitors
Table 18. FireEye Inc. Phishing Protection Major Business
Table 19. FireEye Inc. Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 20. FireEye Inc. SWOT Analysis
Table 21. FireEye Inc. Phishing Protection Product and Solutions
Table 22. FireEye Inc. Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 23. BAE Systems Corporate Information, Location and Competitors
Table 24. BAE Systems Phishing Protection Major Business
Table 25. BAE Systems Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 26. BAE Systems SWOT Analysis
Table 27. BAE Systems Phishing Protection Product and Solutions
Table 28. BAE Systems Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 29. GreatHorn, Inc. Corporate Information, Location and Competitors
Table 30. GreatHorn, Inc. Phishing Protection Major Business
Table 31. GreatHorn, Inc. Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 32. GreatHorn, Inc. SWOT Analysis
Table 33. GreatHorn, Inc. Phishing Protection Product and Solutions
Table 34. GreatHorn, Inc. Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 35. Microsoft Corporation Corporate Information, Location and Competitors
Table 36. Microsoft Corporation Phishing Protection Major Business
Table 37. Microsoft Corporation Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 38. Microsoft Corporation SWOT Analysis
Table 39. Microsoft Corporation Phishing Protection Product and Solutions
Table 40. Microsoft Corporation Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 41. Intel Corporation Corporate Information, Location and Competitors
Table 42. Intel Corporation Phishing Protection Major Business
Table 43. Intel Corporation Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 44. Intel Corporation SWOT Analysis
Table 45. Intel Corporation Phishing Protection Product and Solutions
Table 46. Intel Corporation Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 47. Proofpoint, Inc. Corporate Information, Location and Competitors
Table 48. Proofpoint, Inc. Phishing Protection Major Business
Table 49. Proofpoint, Inc. Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 50. Proofpoint, Inc. SWOT Analysis
Table 51. Proofpoint, Inc. Phishing Protection Product and Solutions
Table 52. Proofpoint, Inc. Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 53. Symantec Corporation Corporate Information, Location and Competitors
Table 54. Symantec Corporation Phishing Protection Major Business
Table 55. Symantec Corporation Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 56. Symantec Corporation SWOT Analysis
Table 57. Symantec Corporation Phishing Protection Product and Solutions
Table 58. Symantec Corporation Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 59. Phishlabs Corporate Information, Location and Competitors
Table 60. Phishlabs Phishing Protection Major Business
Table 61. Phishlabs Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 62. Phishlabs SWOT Analysis
Table 63. Phishlabs Phishing Protection Product and Solutions
Table 64. Phishlabs Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 65. Mimecast Ltd. Corporate Information, Location and Competitors
Table 66. Mimecast Ltd. Phishing Protection Major Business
Table 67. Mimecast Ltd. Phishing Protection Total Revenue (USD Million) (2017-2018)
Table 68. Mimecast Ltd. SWOT Analysis
Table 69. Mimecast Ltd. Phishing Protection Product and Solutions
Table 70. Mimecast Ltd. Phishing Protection Revenue (USD Million), Gross Margin and Market Share (2018-2019)
Table 71. Global Phishing Protection Revenue (Million USD) by Players (2015-2020)
Table 72. Global Phishing Protection Revenue Share by Players (2015-2020)
Table 73. Global Phishing Protection Revenue (Million USD) by Regions (2015-2020)
Table 74. Global Phishing Protection Revenue Market Share by Regions (2015-2020)
Table 75. North America Phishing Protection Revenue by Countries (2015-2020)
Table 76. North America Phishing Protection Revenue Market Share by Countries (2015-2020)
Table 77. Europe Phishing Protection Revenue (Million USD) by Countries (2015-2020)
Table 78. Asia-Pacific Phishing Protection Revenue (Million USD) by Countries (2015-2020)
Table 79. South America Phishing Protection Revenue by Countries (2015-2020)
Table 80. South America Phishing Protection Revenue Market Share by Countries (2015-2020)
Table 81. Middle East and Africa Phishing Protection Revenue (Million USD) by Countries (2015-2020)
Table 82. Middle East and Africa Phishing Protection Revenue Market Share by Countries (2015-2020)
Table 83. Global Phishing Protection Revenue (Million USD) by Type (2015-2020)
Table 84. Global Phishing Protection Revenue Share by Type (2015-2020)
Table 85. Global Phishing Protection Revenue Forecast by Type (2021-2025)
Table 86. Global Phishing Protection Revenue by Application (2015-2020)
Table 87. Global Phishing Protection Revenue Share by Application (2015-2020)
Table 88. Global Phishing Protection Revenue Forecast by Application (2021-2025)
Table 89. Global Phishing Protection Revenue (Million USD) Forecast by Regions (2021-2025)
List of Figures
Figure 1. Phishing Protection Picture
Figure 2. Global Phishing Protection Revenue Market Share by Type in 2019
Figure 3. Email based Phishing Picture
Figure 4. Non-email based Phishing Picture
Figure 5. Phishing Protection Revenue Market Share by Application in 2019
Figure 6. BFSI Picture
Figure 7. Government Picture
Figure 8. Healthcare Picture
Figure 9. Telecommunication and IT Picture
Figure 10. Transportation Picture
Figure 11. Education Picture
Figure 12. Retail Picture
Figure 13. Global Phishing Protection Revenue (USD Million) and Growth Rate (2015-2025)
Figure 14. North America Phishing Protection Revenue (Million USD) and Growth Rate (2015-2025)
Figure 15. Europe Phishing Protection Revenue (Million USD) and Growth Rate (2015-2025)
Figure 16. Asia-Pacific Phishing Protection Revenue (Million USD) and Growth Rate (2015-2025)
Figure 17. South America Phishing Protection Revenue (Million USD) and Growth Rate (2015-2025)
Figure 18. Middle East and Africa Phishing Protection Revenue (Million USD) and Growth Rate (2015-2025)
Figure 19. Global Phishing Protection Revenue (Million USD) and Growth Rate (2015-2025)
Figure 20. Global Phishing Protection Revenue Share by Players in 2019
Figure 21. Global Top 5 Players Phishing Protection Revenue Market Share in 2019
Figure 22. Global Top 10 Players Phishing Protection Revenue Market Share in 2019
Figure 23. Key Players Market Share Trend
Figure 24. Global Phishing Protection Revenue (Million USD) and Growth Rate (%) (2015-2020)
Figure 25. Global Phishing Protection Revenue Market Share by Regions (2015-2020)
Figure 26. Global Phishing Protection Revenue Market Share by Regions in 2018
Figure 27. North America Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 28. Europe Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 29. Asia-Pacific Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 30. South America Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 31. Middle East and Africa Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 32. North America Phishing Protection Revenue Market Share by Countries (2015-2020)
Figure 33. North America Phishing Protection Revenue Market Share by Countries in 2019
Figure 34. USA Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 35. Canada Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 36. Mexico Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 37. Europe Phishing Protection Revenue Market Share by Countries (2015-2020)
Figure 38. Europe Phishing Protection Revenue Market Share by Countries in 2019
Figure 39. Germany Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 40. UK Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 41. France Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 42. Russia Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 43. Italy Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 44. Asia-Pacific Phishing Protection Revenue Market Share by Countries (2015-2020)
Figure 45. Asia-Pacific Phishing Protection Revenue Market Share by Countries in 2019
Figure 46. China Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 47. Japan Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 48. Korea Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 49. India Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 50. Southeast Asia Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 51. South America Phishing Protection Revenue Market Share by Countries (2015-2020)
Figure 52. South America Phishing Protection Revenue Market Share by Countries in 2019
Figure 53. Brazil Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 54. Argentina Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 55. Middle East and Africa Phishing Protection Revenue Market Share by Countries (2015-2020)
Figure 56. Middle East and Africa Phishing Protection Revenue Market Share by Countries in 2019
Figure 57. Saudi Arabia Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 58. UAE Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 59. Egypt Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 60. South Africa Phishing Protection Revenue and Growth Rate (2015-2020)
Figure 61. Global Phishing Protection Revenue Share by Type (2015-2020)
Figure 62. Global Phishing Protection Revenue Share by Type in 2019
Figure 63. Global Phishing Protection Market Share Forecast by Type (2021-2025)
Figure 64. Global Email based Phishing Revenue Growth Rate (2015-2020)
Figure 65. Global Non-email based Phishing Revenue Growth Rate (2015-2020)
Figure 66. Global Phishing Protection Revenue Share by Application (2015-2020)
Figure 67. Global Phishing Protection Revenue Share by Application in 2019
Figure 68. Global Phishing Protection Market Share Forecast by Application (2021-2025)
Figure 69. Global BFSI Revenue Growth Rate (2015-2020)
Figure 70. Global Government Revenue Growth Rate (2015-2020)
Figure 71. Global Healthcare Revenue Growth Rate (2015-2020)
Figure 72. Global Telecommunication and IT Revenue Growth Rate (2015-2020)
Figure 73. Global Transportation Revenue Growth Rate (2015-2020)
Figure 74. Global Education Revenue Growth Rate (2015-2020)
Figure 75. Global Retail Revenue Growth Rate (2015-2020)
Figure 76. Global Phishing Protection Revenue (Million USD) and Growth Rate Forecast (2021-2025)
Figure 77. Global Phishing Protection Revenue (Million USD) Forecast by Regions (2021-2025)
Figure 78. Global Phishing Protection Revenue Market Share Forecast by Regions (2021-2025)
Figure 79. North America Phishing Protection Revenue Market Forecast (2021-2025)
Figure 80. Europe Phishing Protection Revenue Market Forecast (2021-2025)
Figure 81. Asia-Pacific Phishing Protection Revenue Market Forecast (2021-2025)
Figure 82. South America Phishing Protection Revenue Market Forecast (2021-2025)
Figure 83. Middle East and Africa Phishing Protection Revenue Market Forecast (2021-2025)
Figure 84. Sales Channel: Direct Channel vs Indirect Channel
Market research is a method of gathering, assessing and deducing data & information about a particular market. Market research is very crucial in these days. The techniques analyze about how a product/service can be offered to the market to its end-customers, observe the impact of that product/service based on the past customer experiences, and cater their needs and demands. Owing to the successful business ventures, accurate, relevant and thorough information is the base for all the organizations because market research report/study offers specific market related data & information about the industry growth prospects, perspective of the existing customers, and the overall market scenario prevailed in past, ongoing present and developing future. It allows the stakeholders and investors to determine the probability of a business before committing substantial resources to the venture. Market research helps in solving the marketing issues challenges that a business will most likely face.
Market research is valuable because of the following reasons:
Our research report features both the aspects; qualitative and quantitative. Qualitative part provides insights about the market driving forces, potential opportunities, customer’s demands and requirement which in turn help the companies to come up with new strategies in order to survive in the long run competition. The quantitative segment offers the most credible information related to the industry. Based on the data gathering, we use to derive the market size and estimate their future growth prospects on the basis of global, region and country.
Our market research process involves with the four specific stages.
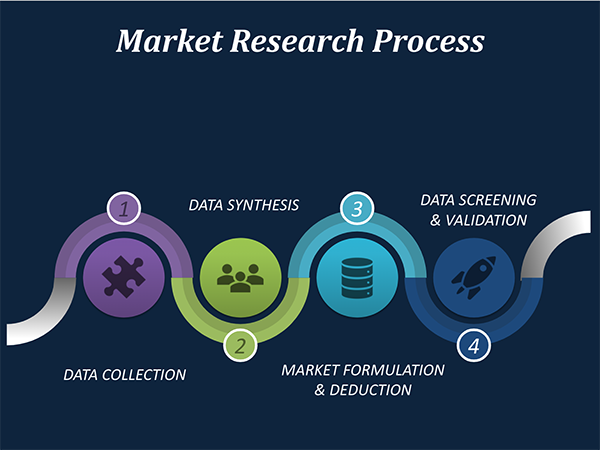
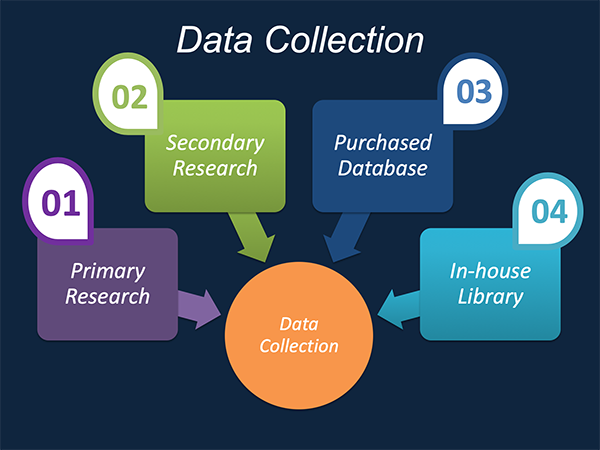
Data Collection: This stage of the market research process involves with the gathering and collecting of the market/industry related data from the sources. There are basically two types of research methods:
Data Synthesis: This stage includes the evaluation and assessment of all the data acquired from the primary and secondary research. It likewise includes in evaluating the information for any disparity watched while information gathering identified with the market. The data & information is gathered with consideration to the heterogeneity of sources. Scientific and statistical methods are implemented for synthesizing dissimilar information sets and provide the relevant data which is fundamental for formulating strategies. Our organization has broad involvement with information amalgamation where the information goes through different stages:
Market Formulation & Deduction: The last stage includes assigning the data & information in a suitable way in order to derive market size. Analyst reviews and domain based opinions based on holistic approach of market estimation combined with industry investigation additionally features a crucial role in this stage.
This stage includes with the finalization of the market size and numbers that we have gathered from primary and secondary research. With the data & information addition, we ensure that there is no gap in the market information. Market trend analysis is finished by our analysts by utilizing data extrapolation procedures, which give the most ideal figures to the market.
Data Validation: Validation is the most crucial step in the process. Validation & re-validation through scientifically designed technique and process that helps us finalize data-points to be used for final calculations. This stage also involves with the data triangulation process. Data triangulation generally implicates the cross validation and matching the data which has been collected from primary and secondary research methods.













































Free Customization
Countries can be added on demand
Free yearly update on purchase of Multi/Corporate User License
Companies served till date

We serve our customers 24x7 for 365 days through calls, emails and live chat options.

Huge database of exceptional market reports bringing market intelligence to your fingertips.

SSL enabled, we offer you various secured payment options for risk free purchase.